Introduction
Software supply chain attacks are rapidly becoming more problematic for global organizations, as the number of companies that depend on an interconnecting web of software packages continues to rise. As the threat continues to make itself known, more companies are trying to implement strategies and improve their internal security measures in order to limit the potential damage that attackers can cause. Despite this, it’s not always easy, and cybersecurity is a perpetual relay race between security professionals and hackers, with software supply chain attacks being one of the current legs of the race.
What are Software Supply Chain Attacks?
Software supply chain attacks happen when a would-be attacker manipulates the code of a software application, which allows them to hijack other applications further along the chain. This allows the attackers to either corrupt data in the network, steal important and valuable information, or gain entry to other parts of the network through a process known as lateral movement. Essentially, a software supply chain attack focuses on attacking the least secure part of the network, and seizing control from there – looking for the metaphorical chink in your armor.
What are the Best Methods to Prevent Attacks?
No security is completely faultless; you could follow every step correctly and you could still be vulnerable in some way. Even the world’s largest companies, with unimaginable resources such as Equifax have seen a severe breach, affecting more than 100 Million customers.
Given such scenarios, you want to limit your exposure as much as possible in order to minimize your chances of falling victim to software supply chain attacks. Below are some easy methods to help you improve your security:
Limit Your Use of External Software
Of course, as a modern business, you can’t be expected to do away with your entire software stack to avoid cyber attacks. However, you can cut out any software that isn’t essential or regularly used. This will help minimize the potential avenues available for a hacker to use to access your network and move laterally to other parts of it, which will in turn, help prevent any attacks.
Regularly Engage with Your Software Suppliers
This is a great way to keep up to date with the latest best practices from all of your suppliers. You will want to keep in contact with every single one of them and monitor their security situation so you can limit your own potential vulnerabilities. If you’re finding that a supplier’s response to your engagement is lacking, then you can consider the possibility of using a different vendor that places a higher priority on your security.
Keep Your Tools Up to Date
This may seem quite obvious, but if you’re using a large number of software packages in your business, you need to make sure you’re always updating them to the latest version. Failing to do this means that you will be working on old versions of your software, which will inevitably be much easier to breach as you won’t be downloading patches to deal with any vulnerabilities in the code. Furthermore, making sure everything is completely updated will also diminish the chances of technical issues unrelated to hacking.
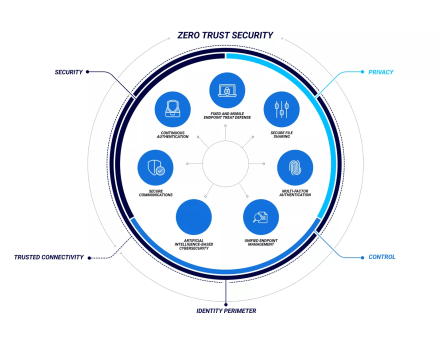
Use Zero-Trust Authentication
Zero-trust authentication runs with the premise that all network activity is automatically deemed to be malicious. As a result, each user will need to go through a set of policy-driven authentication steps in order to gain access to the network. This is a very effective way of limiting the potential of software supply chain attacks as an attacker would need to get through to your authentication process in order to actually gain access to your network.
Examples of Software Supply Chain Attacks
There are numerous examples of software supply chain attacks in recent years, with the most well-known of these having large impacts on the organizations. Each of these cases provides us with a new opportunity to learn and implement new best practices for cybersecurity:
Mimecast
In 2021, the cloud cybersecurity company Mimecast announced that cyber criminals had compromised a certificate that they used to authenticate their services on Microsoft 365 Exchange Web Services. 10% of their user base relied on applications that needed the breached certificate, although they insisted the number of users affected was much smaller.
SolarWinds
In 2020, SolarWinds suffered a massive software supply chain attack, where 18,000 of their business customers, including multiple tech giants like Microsoft had downloaded a backdoor, which was hidden in the Orion IT Management app’s update tool. Microsoft themselves, in turn, had to notify 40 of their customers of the security breach.
Dependency Confusion
In 2021, a security professional named Alex Birsan managed to breach the systems of a number of tech giants such as Microsoft, Apple, Uber and Tesla through the use of a novel attack technique. Birsan sent fake packets of information to a large number of high-profile targets without the use of social engineering techniques.
Conclusion
In closing, you should now know more about what software supply chain attacks are and why they pose such a big risk to modern businesses. Furthermore, you’ve seen some examples of how even the largest companies with the biggest budgets for IT can be at risk with such attacks. The best way for you to protect yourself and your customers whose data you control is to make use of industry best practices and up-to-date tools to make the job easier for your security experts. Following these steps doesn’t make the chance of an attack 0%, but it makes it a lot smaller.




